|
|
|
How does
niceNobody™ work?
Initial setup
Track real ID of anonymous account
Monitor anonymous accounts of blacklist
member |
|
Initial setup |
 |
| |
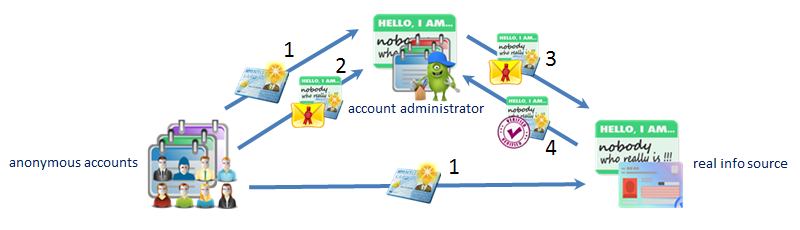
All account holders including
criminals can be anonymous. |
|
| |
The account administrator doesn't
know the real identities of the
account holders. |
|
| |
Real info source, that the account
holder has another account, knows
the identity of the account holder,
including name, mailing address,
email address, phone number, etc. |
|
| |
Step #1, every account holder
provides the account holder's
authentication info called
niceAuthen™, to the account
administrator and the real info
source. |
|
| |
Step #2, the account holder provides
the account holder's encrypted real info
source account ID, which only the
real info source can decrypt, to the
account administrator. |
|
| |
Step #3, after receiving the
encrypted account holder's real info
source account ID, the account
administrator passes it to the real
info source. |
|
| |
Step #4, the real info source
matches the account holder's
niceAuthen™ received from the
account administrator and the one
received from the account holder to
build a link between the anonymous
account and the real info source
account. |
|
| |
Therefore, the account administrator
doesn't know the account holder's
real info source account ID, and the
real info source doesn't know the
account holder's account ID. The
account holder is anonymous both to
the account administrator and the
real info source. |
|
|
|
|
|
Track real ID of anonymous account |
 |
| |
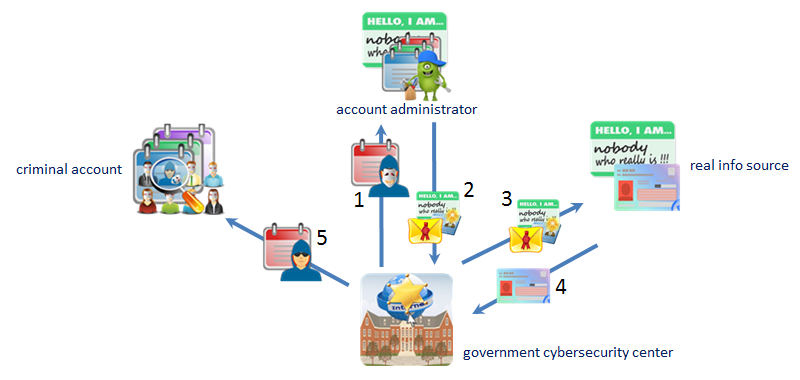
If there is an anonymous illegal or
criminal account, and government
cybersecurity center wants to track
the real ID of the account holder. |
|
| |
Step #1, government cybersecurity
center provides the account
administrator with the anonymous
account ID. |
|
| |
Step #2, the account administrator
provides government cybersecurity
center with the encrypted account
holder's real info source account
ID. |
|
| |
Step #3, government cybersecurity
center provides the real info source
with the encrypted account holder's
real info source account ID. |
|
| |
Step #4, real info source provides
government cybersecurity center with
the real ID of the anonymous account
holder. |
|
| |
Step #5, with the real ID of the
anonymous account holder, government
cybersecurity center can take legal
action. |
|
|
|
|
|
Monitor anonymous accounts of blacklist
member |
 |
| |
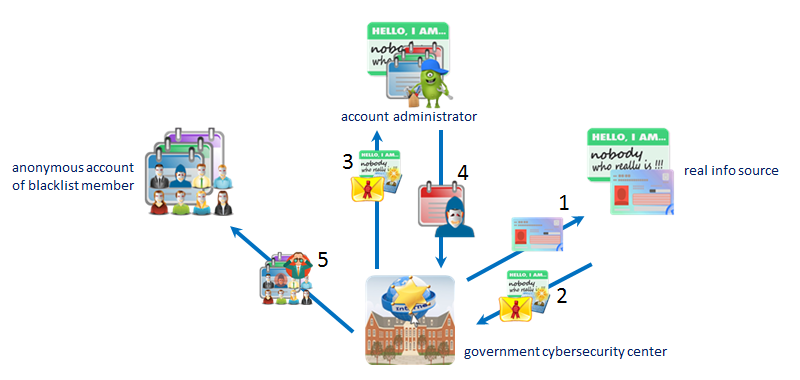
Suppose government cybersecurity center
has a blacklist and wants to monitor
activities of anonymous accounts of
blacklist members. |
|
| |
Step #1, government cybersecurity center
provides real info source with the
blacklist member's ID. |
|
| |
Step #2, the real info source provides
government cybersecurity center with the
encrypted account holder's real info
source account ID. |
|
| |
Step #3, government cybersecurity center
provides the account administrator with
the encrypted account holder's real
info source account ID. |
|
| |
Step #4, according to the record of the
encrypted account holder's real
info source account ID, the
account administrator provides
government cybersecurity center with the
anonymous account ID. |
|
| |
Step #5, knowing the anonymous account
ID of the blacklist member, government
cybersecurity center can monitor the
anonymous account activity. |
|
|
|
|
|
|
|
The Nicest Source of
Real Info
Banks
Encourage Banks to Participate |
|
Banks |
 |
Banks have been collecting real info
about account holders for decades. |
|
 |
Banks conduct the most rigorous
on-site inspection of account holders'
photo IDs. |
|
 |
For internet account holders who do
not have a bank account, it is
convenient to open a new bank account. |
|
 |
For a minor without a bank account,
guardian's authentication info
niceAuthen™ can
be used to authenticate the minor's
identity. |
|
|
|
|
|
Encourage Banks to Participate |
|
If banks or other financial institutions
participate in niceNobody™ program
to support government demands for
cybersecurity,
they can propose license fees (nicePrice™)
to leverage
niceFinTech™ products
to dominate the fintech market
with international patented innovative
technologies.
Discard account passwords to eliminate
all kinds of frauds. |
| |
* nicePay™
The
buyer pays the seller directly through their banks.
All
the involving parties, the buyer, the seller, the
buyer's bank and the seller's bank are
authenticated.
The
buyer can be anonymous to the seller, including the
payment account ID.
Trade
order with payment terms has electronic signatures
of the buyer and the seller.
If
there is any dispute, the seller can track the
buyer's real info. Either party can use the
trade order with electronic signatures to solve
the problem in accordance with legal procedures. |
 |
| |
* niceCreditCard™
Any
bank can issue its own credit card.
Payments are only processed between the bank that
issued the credit card and the bank that receives
the payment.
All
parties involved are authenticated.
The
name and credit card number of the credit card
holder can be anonymous to the payee and the bank
that receives the payment. |
 |
| |
* niceRemit™
Subject to the restrictions on international
remittances in various countries, anyone can remit
money to anyone globally at any time, without going
to the bank counter for on-site process or setting
up the beneficiary's bank account in advance.
Both
the remitter and beneficiary are authenticated. |
 |
| |
* niceCash™
Subject to restrictions on international remittances
in various countries, anyone can reliably withdraw
cash from her/his bank account in their home country
at ATMs around the world.
|
 |
| |
* niceLoan™
Online processing loan applications
with identity authentication of the
loan agent and the loan applicant,
electronic signatures of all
documents. |
 |
| |
* niceInsurance™
Online processing insurance
applications with identity
authentication of the insurance
agent and the policyholder,
electronic signatures of all
documents. |
 |
| |
* nicePension™
Manage pension account online,
authenticate the account holder's
identity, electronic signatures of
all account holder's instructions
and the service agent's replies. |
 |
| |
* niceStocks™
Online stock trading, authenticate
the account holder's identity,
electronic signatures of all account
holder's instructions and the
service agent's replies. |
 |
|
|
|
|
|
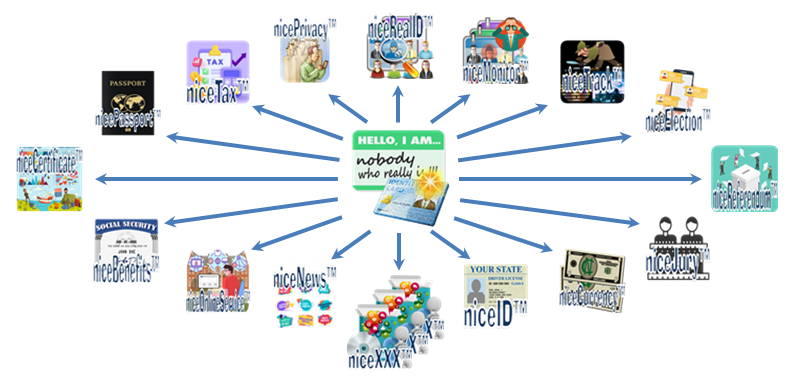
niceNobody™ Applications
niceNobody™
is related to many applications that improve security,
reliability and convenience. |
 |
 |
* nicePrivacy™
Normal internet accounts can be 100% anonymous to
account administrators and other netizens.
|
|
 |
* niceRealID™
For an
anonymous illegal or criminal internet account, government
agencies can track down the real identity of the
account holder.
|
|
 |
* niceMonitor™
For a
blacklist member, government agencies can monitor
the blacklist member's anonymous accounts.
|
|
 |
* niceTax™
Eliminates tax refund fraud.
|
|
 |
* nicePassport™
Provide reliable and convenient online issuance of
digital passports.
|
|
 |
* niceCertificate™
Provide reliable and convenient online issuance of
documents such as fishing licenses.
|
|
 |
* niceBenefits™
Provide reliable and convenient online services of
social benefits.
|
|
 |
* niceOnlineService™
Provide reliable and convenient government online
services.
|
|
 |
* niceNews™
Fight
fake news by tracking the real IDs of sources and
publishers for legal action.
|
|
 |
* niceTrack™
Strictly control the flow of strategic technologies and
products.
|
|
 |
* niceElection™
Provide effective and reliable voting, with
traceability of anonymous voters.
|
|
 |
* niceReferendum™
Provide effective and reliable referendum, with
traceability of anonymous voters.
|
|
 |
* niceJury™
Offer
the convenience and reliability of jury duty with
anonymous and remote options.
|
|
 |
* niceCurrency™
Provide a reliable and secure digital currency
system.
|
|
 |
* niceID™
Provide a reliable, fake less and convenient
digital ID system.
|
|
 |
* niceXXX™
There
are 94 other niceXXX cyber systems based on
niceNobody™
that are very useful for governments, companies,
banks, schools, etc.
|
|
|
|
|
|
|
|
|